Category 6 cable, usually Cat-6, is a cable standard for Gigabit Ethernet and other network protocols that is backward compatible with the Category 5/5e and Category 3 cable standards. The main difference between Cat-6 and it’s previous versions is that CAT-6 fully utilizes all four pairs. Cat-6 features more stringent specifications for crosstalk and system noise. The cable standard provides performance of up to 250 MHz and is suitable for 10BASE-T / 100BASE-TX and 1000BASE-T / 1000BASE-TX (Gigabit Ethernet). It is expected to suit the 10GBASE-T (10Gigabit Ethernet) standard, although with limitations on length if unshielded Cat 6 cable is used.
The cable contains four twisted copper wire pairs, just like earlier copper cable standards and when used as a patch cable, Cat-6 is normally terminated in 8P8C modular connectors. Some Cat-6 cables are too large and may be difficult to attach to 8P8C connectors without a special modular piece and are technically not standard compliant. If components of the various cable standards are intermixed, the performance of the signal path will be limited to that of the lowest category. The maximum allowed length of a Cat-6 cable is 100 meters.
The cable is terminated in either the T568A scheme or the T568B scheme. It doesn’t make any difference which is used, as they are both straight through:

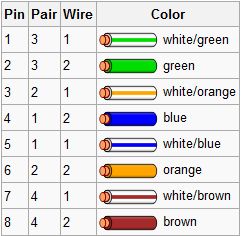
Crossover is used for hub to hub, computer to computer, wherever two-way communication is necessary. All gigabit ethernet equipment, and most new 10/100Mb equipment, supports automatic crossover, meaning that either a straight-through or crossover cable may be used for any connection. However, older equipment requires the use of a straight-through cable to connect a switch to a client device, and a crossover cable to connect a switch to a switch or a client to a client. Crossover cables can be constructed by wiring one end to the T568A scheme and the other end with the T568B scheme. This will ensure that the Transmit (TX) pins on both ends are wired through to the Receive (RX) pins on the other end.
If you are starting to build a LAN network now, it’s recommend to use already CAT-6 as it can accommodate most of the usual traffic in a network based on the fact that already NIC cards are build for the speed of 1Gbps. Some useful tips regarding the use of CAT-6 and any Ethernet cable are:
– Do run cables over distances up to 100 meters with their rated speed
– If you know how to handle some cabling tools, do make your own cable if you need lots of varying lengths
– Don’t order anything less than Cat. 5e cable
– Don’t crimp or staple cable, this can easily cause breaks in the cable which are sometimes hard to track down
– Ethernet cables are not directional in any way, you cannot install one backwards
– Lighter colored cables are usually a better choice for two reasons: They are easier to see in the dark, and it’s easier to read the cable catogory stamped on the side
– Use a patch cable when connecting a computer to a router or hub, use a cross over cable when connecting two computers directly together
– If it’s possible and you know that you need higher speed that 100Mbps do not mix different type of cables on the same network segment
– Even if all the specification are saying that the CAT-6 is protected against external factors, do not mount this cables close by cable power or any other cable that can influence the performance of Ethernet cable.
Below you can find a presentation of CAT-6 “how-to” thanks to Giganet:
[flashvideo filename=https://ipnet.xyz/vid/hardware/archive/2009/04/Category6UTPTermination.flv image=https://ipnet.xyz/vid/hardware/archive/2009/04//Category6UTPTermination.jpg width=486 height=412 /]
Resources used:
http://donutey.com/ethernet.php
http://en.wikipedia.org/wiki/Category_6_cable
http://en.wikipedia.org/wiki/TIA/EIA-568-B

 Now and then, especially when you expect less, the network crashes or encounter an issue and then you had to troubleshoot. Sometime the problem is right there, you can see it and it’s easy to fix, but in other cases you’ll have to put an eye in the packets that are traveling through it and search deeper for the solution. When it comes to network sniffing or packet capturing or whatever you want to call it, I believe that the name
Now and then, especially when you expect less, the network crashes or encounter an issue and then you had to troubleshoot. Sometime the problem is right there, you can see it and it’s easy to fix, but in other cases you’ll have to put an eye in the packets that are traveling through it and search deeper for the solution. When it comes to network sniffing or packet capturing or whatever you want to call it, I believe that the name